
Research Results of Data Driven Software Technology Lab Won the ACM SIGSOFT Distinguished Paper Award at ICSE 2023
Recently, ICSE 2023 (International Conference on Software Engineering), a flagship conferences in the field of software engineering, was successfully held in Melbourne, Australia. Paper “Lejacon: A Lightweight and Efficient Approach to Java Confidential Computing on SGX” from the Data Driven Software Technology Laboratory (DDST) in the Department of Computer Science and Engineering won the ACM SigSoft Distinguished Paper Award at the conference. It is the first time for Shanghai Jiao Tong University to win this award.

Lejacon is a novel approach to Java confidential computing. It takes a balance between Java’s platform independence and necessity of native execution in enclaves by a demand-driven programming paradigm, an SCW-directed separate compilation technique, and a runtime system for running confidential Java code. Lejacon is effective in protecting confidential Java applications, reducing their TCB sizes and in-enclave memory footprints at runtime.
Motivation
Intel’s SGX is a confidential computing technique. It allows key functionalities of C/C++/native applications to be confidentially executed in hardware enclaves. However, numerous cloud applications are written in Java. For supporting their confidential computing, state-of-the-art approaches deploy Java Virtual Machines (JVMs) in enclaves and perform confidential computing on JVMs. Meanwhile, these JVM-in-enclave solutions still suffer from serious limitations, such as heavy overheads of running JVMs in enclaves, large attack surfaces, and deep computation stacks.
Approach & Result
To mitigate the above limitations, the authors formalize a Secure Closed-World (SCW) principle and then propose Lejacon, a lightweight and efficient approach to Java confidential computing. The key idea is, given a Java application, to (1) separately compile its confidential computing tasks into a bundle of Native Confidential Computing (NCC) services; (2) run the NCC services in enclaves on the Trusted Execution Environment (TEE) side, and meanwhile run the non-confidential code on a JVM on the Rich Execution Environment (REE) side. The two sides interact with each other, protecting confidential computing tasks and as well keeping the Trusted Computing Base (TCB) size small.
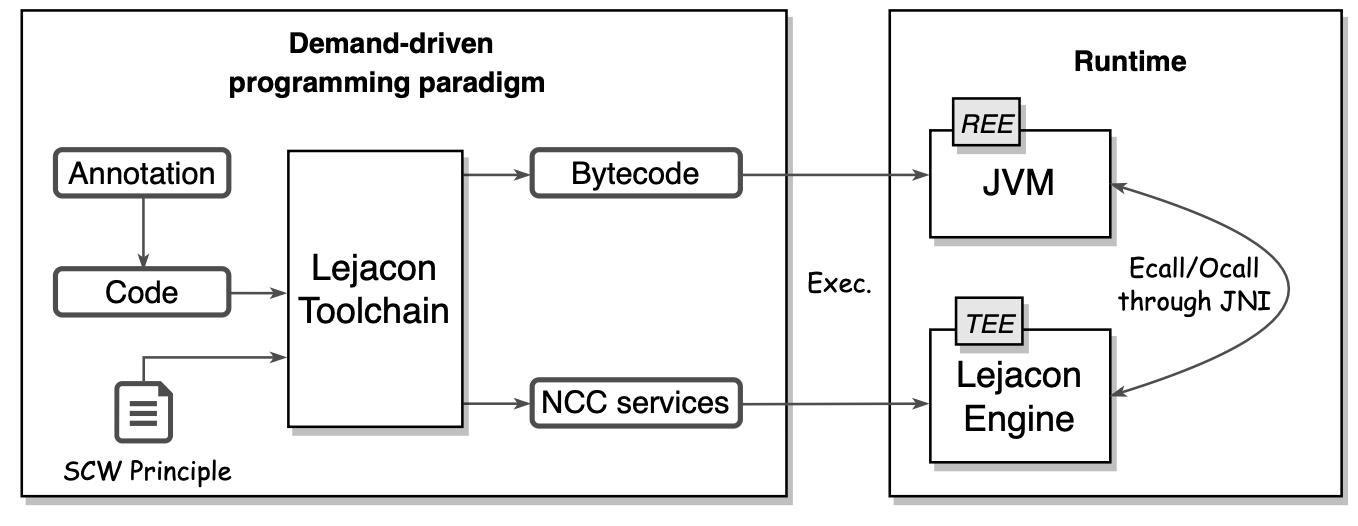
Fig. An overview of Lejacon
The authors implement Lejacon and evaluate it against OcclumJ (a state-of-the-art JVM-in-enclave solution) on a set of benchmarks using the BouncyCastle cryptography library. The evaluation results clearly show the strengths of Lejacon: it achieves competitive performance in running Java confidential code in enclaves; compared with OcclumJ, Lejacon achieves speedups by up to 16.2× in running confidential code and also reduces the TCB sizes by 90+% on average.
About the authors

Xinyuan Miao (First author)

Yuting Chen (Corresponding author)
The first author is Phd student Xinyuan Miao and the corresponding author is associate Prof. Yuting Chen from the CS Department of SJTU. The paper was completed with cooperators from Aliyun and Dalian University of Technology.
About the conference and the award
ICSE, the IEEE/ACM International Conference on Software Engineering, is the premier software engineering conference. Since 1975, ICSE provides a forum where researchers, practitioners, and educators gather together to present and discuss the most recent innovations, trends, experiences and issues in the field of software engineering.
ACM SIGSOFT Distinguished Paper Awards are awarded only to full-length technical papers accepted by the program committee for the main track of a SIGSOFT-sponsored meeting. In this year, the award committee selected 10 outstanding manuscripts (i.e., less than 5% of the accepted papers)

